#malware c2
Explore tagged Tumblr posts
Text
Google Shuts Down China-Linked Calendar Hack: APT41 Malware Exposed
Introduction In a stunning revelation, Google has confirmed that state-sponsored hackers from China exploited Google Calendar to run a sophisticated cyber-espionage campaign. The operation, linked to the APT41 (also known as HOODOO) group, utilized Calendar events as a command-and-control (C2) channel to extract sensitive data from infected devices. Discovery and Attribution According to…
#apt41#cloud app hack#cyber espionage china#cyberattack 2025#dll injection#google calendar hack#google safe browsing#google threat intel#gtig#malware c2#malware via calendar#plustdrop#process hollowing#spear phishing#toughprogress malware
0 notes
Text
Akira ransomware prevention and defense 2024
New Post has been published on https://thedigitalinsider.com/akira-ransomware-prevention-and-defense-2024/
Akira ransomware prevention and defense 2024


EXECUTIVE SUMMARY:
In March of 2023, the first Akira ransomware strain was observed in the wild. Since then, the group has compromised over 100 different organizations, targeting those in the financial, manufacturing, real-estate, healthcare and medical sectors.
Akira operates on a Ransomware-as-a-Service (RaaS) model and typically deploys a double-extortion scheme. This involves exfiltrating sensitive data prior to device encryption and insisting on a ransom in exchange for withholding the data from the group’s TOR leak site.
Most recently, Akira interrupted a U.S. emergency dispatch system, causing a nine-day operational outage. During the outage, dispatchers relied on backup systems. As of the present writing, full system restoration is still a work-in-progress.
About Akira
The group is believed to have taken its name from the 1988 cult anime film of the same name, which depicts biker gangs in a dystopian Tokyo. The Akira ransomware gang is known for use of a retro aesthetic on victims’ sites, reminiscent of the 1980’s green screen consoles.
Cyber security researchers have uncovered evidence linking the Akira group to the notorious Conti ransomware operation. In at least three separate cryptocurrency transactions, Akira criminals appear to have sent the full amount of the ransom payment to Conti-affiliated addresses.
The overlap of cryptocurrency wallets indicates that the individual controlling the address or wallet has either splintered off from the original group, or is working with two different groups simultaneously.
How Akira operates
Akira commonly breaches systems by obtaining unauthorized access to the target organization’s VPNs, as through a compromised username/password combination.
After sneaking in through an endpoint, Akira typically uses any of several methods to acquire permissions that enable lateral network movement.
These methods include orchestrating a mini-dump of the LSASS (Local Security Authority Subsystem Service) process memory, obtaining credentials stored in the Active Directory database and exploiting known vulnerabilities in backup software.
Advanced persistence mechanisms
Akira ordinarily deploys tools and techniques like Remote Desktop Protocol (RDP), Server Message Block (SMB), impacket module wmiexec, and a service manager tool known as nssm.exe, in order to gain persistence within systems.
As is the case among many cyber criminal groups, Akira also attempts to uninstall or disable security defenses, including anti-malware and network monitoring tools.
Beyond that, the group tends to use the runas command (a Windows command-line tool that allows for the execution of scripts, apps…etc., with different user permissions from the currently logged-in user) in order to execute commands.
This, in turn, makes tracking hacker activities more difficult for defenders.
Akira and C2 mechanisms
Most ransomware attackers weaponize a command and control (C2) mechanism to execute activities. The C2 system establishes communication with and exerts control over a compromised machine or network.
The C2 server can potentially be used to manage the ransomware deployment and to initiate the encryption of data on targeted systems. For the purpose of establishing persistent remote access to multiple systems within the network, Akira seems to prefer AnyDesk.
Akira and data exfiltration
Akira uses a number of different tools when it comes to data exfiltration. These include WinRAR, WinSCP, rclone, and MEGA.
After data exfiltration, Akira demands a ransom from victims. In the event that the ransom goes unpaid, the group will leak stolen data on its TOR site, as previously mentioned.
Akira’s encryption tactic
To encrypt a given target’s data, Akira relies on a combination of AES and RSA algorithms. The group will also purge Windows Shadow Volume Copies from devices by running a PowerShell command. For victims, this massively complicates the process of independently restoring systems and recovering encrypted data.
Recommended means of preventing and defending against Akira’s ransomware
1. Address identity and access management.
Enhance access controls. Implement multi-factor authentication (MFA). Akira can gain initial access via unauthorized logins to VPNs through accounts that lack MFA. This seemingly simplistic safeguard can significantly limit the risk of unauthorized access.
2. Store credentials securely.
As noted earlier, Akira deploys a variety of tactics to obtain credentials. These tactics include execution of a mini-dump of the LSASS process memory, retrieving credentials stored in the Active Directory database and leveraging vulnerabilities in backup services.
To that effect, organizations need to take care when it comes to credential management. Credentials should be stored securely, and regularly updated. Backup services must also be appropriately secured.
3. Elevate your patch management protocol.
Akira commonly exploits vulnerabilities in VPN software. Thus, regular patching and updating of software can proactively prevent Akira attacks.
4. Monitor your network like a ninja.
Akira relies on built-in commands and tools to identify an environment’s systems and to learn about the status of target devices. Detect duplicitous behavior by monitoring for unusual network activity.
Your organization should also monitor for data exfiltration. Look for substantial data transfers and unusual network patterns.
5. Secure C2 channels.
Akira uses widely recognized dual-use agents, such as AnyDesk, to establish persistent remote access. Remain vigilant in regards to abnormal remote access activities and fortify Command and Control (C2) channels. This can be of tremendous assistance when it comes to thwarting potential attacks.
6. Secure remote desktop protocol.
Akira frequently employes Remote Desktop Protocol (RDP), using legitimate local administrator user accounts to facilitate lateral movement. Enhancing the security of RDP and staying vigilant for atypical RDP activity can be effective in preventing lateral movement.
7. Implement endpoint protection.
Akira usually attempts to uninstall endpoint protections as a means of evading detection. Deploying robust endpoint protection measures and consistently monitoring for efforts to disable or uninstall such safeguards can also assist with attack prevention and detection.
Related resources
The 10 most dangerous ransomware groups right now – Read article
Secure your data. Explore endpoint security solutions – Learn more
Identity and access management solution free trial – Click here
#2023#2024#access management#Accounts#active directory#Akira#Akira ransomware#Algorithms#anti-malware#apps#Article#attackers#authentication#backup#Behavior#C2#CISO#command#communication#Conti#Conti ransomware#credential#credentials#cryptocurrency#cyber#cyber security#data#data exfiltration#Database#defenders
0 notes
Link
https://bit.ly/3OEOTfr - 🔒 Cyberattacks have become a major concern, affecting people, organizations, and governments globally. Understanding the anatomy of a cyberattack is key to building effective cybersecurity strategies. This report outlines the essential elements of cyberattacks, and the stages involved in phishing and ransomware attacks. #CyberSecurity #CyberThreats 🕵️ Reconnaissance: In the initial phase, attackers collect data about the target using active or passive techniques to identify vulnerabilities and important assets. #Reconnaissance #CyberAttack 🛠️ Weaponization: Attackers write malicious code or exploit known weaknesses, often creating malware such as viruses, trojans, or ransomware to target systems. #Weaponization #Malware 📨 Delivery: The next stage involves delivering the malicious payload using methods like phishing emails, harmful links, or infected attachments. #EmailPhishing #MaliciousLinks 🚪 Exploitation: Attackers then exploit flaws in the target network or system to gain unauthorized access, utilizing vulnerabilities in software or authentication processes. #Exploitation #UnauthorizedAccess 🔌 Installation: Following successful exploitation, the attackers install the virus to maintain control over the target system and potentially escalate their network access. #MalwareInstallation #NetworkSecurity 🎮 Command and Control (C2): Attackers set up C2 infrastructure for communication with compromised systems, allowing them to secretly execute malicious actions. #CommandControl #C2 🎯 Actions on Objective: Once in control, attackers may pursue goals such as data theft, alteration, ransom requests, or launching further attacks. #DataTheft #Ransomware 🧹 Covering Tracks: The final stage involves erasing evidence by deleting logs and disguising activity to avoid detection. #CoveringTracks #CybersecurityMeasures 🎣 Understanding Phishing Attacks: These involve social engineering to deceive victims into revealing sensitive information, through stages of reconnaissance, weaponization, delivery, exploitation, installation, C2, actions on objective, and covering tracks. #PhishingAttack #SocialEngineering 🔐 Understanding Ransomware Attacks: In a ransomware attack, malicious software encrypts a victim’s data, demanding ransom for decryption. The stages include reconnaissance, weaponization, delivery, exploitation, installation, C2, actions on objective, and covering tracks. #Ransomware #DataEncryption 🛡️ Conclusion: Recognizing the stages of cyberattacks empowers individuals and organizations to implement proactive security measures. Education about potential threats and best practices can defend against the evolving landscape of cyber threats. Cybersecurity is a shared responsibility that requires vigilance and proactive steps to reduce risks.
#CyberSecurity#CyberThreats#Reconnaissance#CyberAttack#Weaponization#Malware#EmailPhishing#MaliciousLinks#Exploitation#UnauthorizedAccess#MalwareInstallation#NetworkSecurity#CommandControl#C2#DataTheft#Ransomware#CoveringTracks#CybersecurityMeasures#PhishingAttack#SocialEngineering#DataEncryption#CybersecurityAwareness#CollectiveResponsibility#ransomwareattacks#ransomwareattack#concern#government#cybersecurity#strategy
0 notes
Text
The README file for the project instruct the victim first to execute the malicious password manager application ('PasswordManager.py') on their system and then start looking for the errors and fixing them.
That file triggers the execution of a base64 obfuscated module hidden in the'_init_.py' files of the 'pyperclip' and 'pyrebase' libraries.
The obfuscated string is a malware downloader that contacts a command and control (C2) server and awaits for commands. Fetching and running additional payloads is within its capabilities.
9 notes
·
View notes
Text
Recent Activities of Transparent Tribe (APT36)

Transparent Tribe, also known as APT36, is a Pakistan-based threat group active since at least 2013. They have consistently targeted Indian government, defence, and aerospace sectors. Recent activities indicate a significant evolution in their tactics and tools.
May 2024: Targeting Indian Defence and Aerospace Sectors

In May 2024, Transparent Tribe intensified cyber-espionage operations against India's defence and aerospace sectors. They employed phishing emails containing malicious attachments or links to deploy various tools, including:
Crimson RAT: A remote access Trojan used for data theft and surveillance.
Poseidon: A Golang-based agent compatible with Linux and macOS systems.
Python-based downloaders: Compiled into ELF binaries to target Linux environments.
The group also exploited India's development of indigenous Linux-based operating systems, such as MayaOS, by distributing Executable and Linkable Format (ELF) binaries to compromise these systems. [Source]
Late 2023 to Early 2024: Evolution of ElizaRAT Malware
Between late 2023 and early 2024, Transparent Tribe advanced their malware capabilities by developing ElizaRAT, a Windows Remote Access Tool. ElizaRAT's evolution included:
Enhanced Evasion Techniques: Improved methods to avoid detection by security systems.
Cloud-Based Command and Control (C2): Utilisation of services like Google Drive, Telegram, and Slack for C2 communications.
Modular Payloads: Deployment of additional payloads such as ApoloStealer for targeted data exfiltration.
These developments indicate a strategic shift towards more sophisticated and flexible attack methodologies. [Source]
September 2023: Infrastructure Expansion and Linux Targeting
In September 2023, investigations revealed that Transparent Tribe expanded their infrastructure, employing Mythic C2 servers hosted on platforms like DigitalOcean. They also began targeting Linux environments by distributing malicious desktop entry files disguised as PDFs. This approach aimed to compromise systems running Linux-based operating systems, aligning with India's adoption of such systems in government sectors. [Source]
June 2023: Focus on Indian Education Sector
By June 2023, Transparent Tribe shifted focus to India's education sector, distributing education-themed malicious documents via phishing emails. These campaigns aimed to deploy Crimson RAT, enabling the group to exfiltrate sensitive information from educational institutions. [Source]
These recent activities demonstrate Transparent Tribe's persistent efforts to adapt and refine their tactics, expanding their target spectrum and enhancing their malware arsenal to effectively compromise systems across various sectors.
Author: Kelly Hector
Blog: Digitalworldvision
2 notes
·
View notes
Text
Massive Malware Campaigns Infiltrate Docker Hub, Deploying Millions of Malicious Containers

JFrog's security research team has uncovered three large-scale malware campaigns infiltrating Docker Hub, a platform facilitating Docker image development, collaboration, and distribution. These campaigns have deployed millions of malicious "imageless" containers, exploiting Docker Hub's community features. Docker Hub hosts a staggering 12.5 million repositories, but according to JFrog, approximately 25% serve no useful functionality. Instead, they act as vehicles for spam, pirated content promotion, and malware dissemination, posing a significant threat to unsuspecting users.
Exploiting Community Features: Malicious Documentation Pages
The attack on Docker Hub exploited its community features, allowing users to publish repositories with only documentation pages, devoid of actual container images. Disguised as legitimate content, these documentation pages lead users to phishing and malware-hosting websites, putting their systems at risk.
Three Major Malware Campaigns Identified
Through an analysis of Docker Hub image creation patterns over the past five years, the research team identified over four million imageless repositories, constituting 37% of all public repositories. Further investigation revealed three main malware campaigns: - Downloader Campaign: Offers pirated content and game cheats as bait. - eBook Phishing Campaign: Lures users with free eBook downloads to steal credit card information. - Website Campaign: Characterized by randomly generated repositories with benign descriptions. Each campaign employed distinct tactics to evade detection, such as URL shorteners and open redirect bugs. The payloads of these campaigns, predominantly Trojans, communicated with command-and-control (C2) servers to download additional malware and execute persistent tasks on infected systems.
Call for Enhanced Moderation and Community Involvement
These findings highlight the need for enhanced moderation on Docker Hub and greater community involvement in detecting and mitigating malicious activity. Andrey Polkovnichenko, security researcher at JFrog, warned, "The most concerning aspect of these three campaigns is that there is not a lot that users can do to protect themselves at the outset other than exercising caution." Polkovnichenko added, "These threat actors are highly motivated and are hiding behind the credibility of the Docker Hub name to lure victims. As Murphy's Law suggests, if malware developers can exploit something, it inevitably will be, so we expect that these campaigns can be found in more repositories than just Docker Hub." Read the full article
2 notes
·
View notes
Text
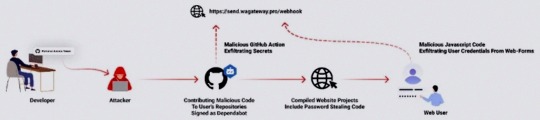
GitHub Repositories Hit by Password-Stealing Commits Disguised as Dependabot Contributions
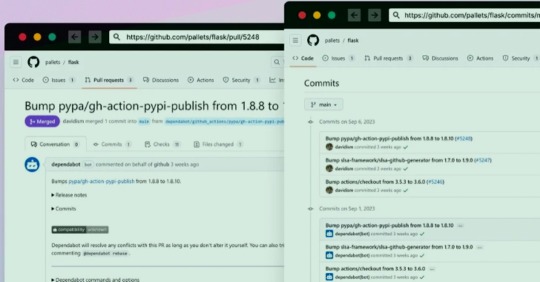
A new deceptive campaign has been observed hijacking GitHub accounts and committing malicious code disguised as Dependabot contributions with an aim to steal passwords from developers.
"The malicious code exfiltrates the GitHub project's defined secrets to a malicious C2 server and modify any existing javascript files in the attacked project with a web-form password-stealer malware code effecting any end-user submitting its password in a web form," Checkmarx said in a technical report
The malware is also designed to capture GitHub secrets and variables to a remote server by means of a GitHub Action.
The software supply chain security firm said it observed the atypical commits to hundreds of public and private GitHub repositories between July 8 and 11, 2023.
It has emerged that the victims had their GitHub personal access tokens stolen and used by the threat actors to make falsified code commits to users' repositories by posing as Dependabot.
Dependabot is designed to alert users of security vulnerabilities in a project's dependencies by automatically generating pull requests to keep them up-to-date.
"The attackers accessed the accounts using compromised PATs (Personal Access Token) -- most likely exfiltrated silently from the victim's development environment," the company said. Most compromised users are located in Indonesia.
However, the exact method by which this theft may have taken place is currently unclear, although it's suspected that it may have involved a rogue package inadvertently installed by the developers.
This is evidenced by a new data exfiltration campaign targeting both npm and PyPI that uses as many as 39 counterfeit packages to gather sensitive machine information and transmit the details to a remote server.
The development highlights the continued attempts on part of threat actors to poison open-source ecosystems and facilitate supply chain compromises.
3 notes
·
View notes
Link
3 notes
·
View notes
Text
Google warns infoseccers: Beware of North Korean spies sliding into your DMs
In the ever-evolving landscape of cybersecurity threats, vigilance remains paramount. Recent reports from Google's Threat Analysis Group (TAG) have unveiled concerning activities involving suspected North Korean-backed hackers. These malicious actors are once again setting their sights on the infosec community, employing familiar tactics and some intriguing new tools.
The Social Engineering Approach
Just as they did in 2021, suspected North Korean agents are employing social engineering tactics to infiltrate the infosec community. They initiate contact through social media platforms, building trust and rapport with potential targets before moving communication to secure services like Signal or WhatsApp. This method allows them to establish a seemingly legitimate connection before launching their cyberattacks.
A Dangerous Payload
Once a relationship is established, the threat actors send a malicious file containing at least one zero-day vulnerability in a popular software package. While Google did not disclose the affected vendor, they assured the public that efforts are underway to deploy a patch. This technique is a stark reminder of the persistent threat posed by zero-day vulnerabilities, which can catch even the most prepared organizations off guard.
The malicious file includes shellcode that collects information from compromised systems and sends it back to command-and-control (C2) servers. This shellcode shares similarities with previous North Korean exploits, indicating a potentially organized and well-equipped threat actor.
A Disturbing Discovery
In addition to the established tactics, Google's TAG uncovered an unsettling development - a standalone tool for Windows named "dbgsymbol." This tool initially appears benign, designed to download debugging symbol information from various sources. Such information is invaluable for debugging software or conducting vulnerability research.
However, there's a dark twist to this tool. It possesses the capability to download and execute arbitrary code from an attacker-controlled domain. This feature raises the stakes significantly, as it can be leveraged to deliver devastating malware payloads.
Staying Safe in a Dangerous Landscape
Given the potential risks, it's crucial for anyone who may have downloaded or run dbgsymbol to take immediate action. Google recommends ensuring your system is in a known clean state, which may require a full reinstallation of the operating system. This precaution is necessary to prevent any hidden malware from compromising your system further.
source- https://www.theregister.com/2023/09/11/infosec_roundup/
1 note
·
View note
Text
A Data Leak Detection Guide for the Tech Industry in 2025

For the tech industry, data is more than just information; it's the lifeblood of innovation, intellectual property, and customer trust. A data leak – the unauthorized exposure of sensitive information – can be an existential threat, far more insidious than a visible malware attack. Leaks can trickle out slowly, going unnoticed for months, or erupt in a sudden torrent, exposing source code, customer PII, design documents, or proprietary algorithms.
In 2025's hyper-connected, cloud-centric, and API-driven world, detecting these leaks is a unique and paramount challenge. The sheer volume of data, the distributed nature of development, extensive third-party integrations, and the high value of intellectual property make tech companies prime targets. Proactive, multi-layered detection is no longer optional; it's essential for survival.
Here's a comprehensive guide to detecting data leaks in the tech industry in 2025:
1. Advanced Data Loss Prevention (DLP) & Cloud Security Posture Management (CSPM)
Gone are the days of basic keyword-based DLP. In 2025, DLP needs to be intelligent, context-aware, and integrated deeply with your cloud infrastructure.
Next-Gen DLP: Deploy DLP solutions that leverage AI and machine learning to understand the context of data, not just its content. This means identifying sensitive patterns (e.g., PII, PHI, financial data), source code fragments, and intellectual property across endpoints, networks, cloud storage, and collaboration tools. It can detect unusual file transfers, unauthorized sharing, or attempts to print/download sensitive data.
Integrated CSPM: For tech companies heavily invested in cloud, Cloud Security Posture Management (CSPM) is non-negotiable. It continuously monitors your cloud configurations (AWS, Azure, GCP) for misconfigurations that could expose data – like publicly accessible S3 buckets, overly permissive IAM roles, or unencrypted databases. A misconfigured cloud asset is a leak waiting to happen.
2. User and Entity Behavior Analytics (UEBA) Powered by AI
Data leaks often stem from compromised accounts or insider threats. UEBA helps you spot deviations from the norm.
Behavioral Baselines: UEBA tools use AI to learn the "normal" behavior patterns of every user (employees, contractors, customers) and entity (servers, applications) in your environment. This includes typical login times, locations, data access patterns, and resource usage.
Anomaly Detection: When behavior deviates significantly from the baseline – perhaps a developer suddenly downloading gigabytes of source code, an administrator accessing systems outside their routine hours, or a sales executive emailing large customer lists to a personal address – UEBA flags it as a high-risk anomaly, indicating a potential compromise or malicious insider activity.
Prioritized Alerts: UEBA helps cut through alert fatigue by assigning risk scores, allowing security teams to focus on the most critical threats that signify potential data exfiltration.
3. Network Traffic Analysis (NTA) with Deep Packet Inspection
Even if data bypasses endpoint or application controls, it still has to travel across the network. NTA is your eyes and ears for data exfiltration.
Real-time Monitoring: NTA (often part of Network Detection and Response - NDR) continuously monitors all network traffic – internal and external – using deep packet inspection and machine learning.
Exfiltration Signatures: It identifies suspicious patterns like unusually large outbound data transfers, communication with known command-and-control (C2) servers, attempts to tunnel data over non-standard ports, or encrypted traffic to unusual destinations.
Detecting Post-Compromise Movement: NTA is crucial for detecting lateral movement by attackers within your network and the final stages of data exfiltration, often providing the earliest warning of a breach in progress.
4. Specialized Source Code & Repository Monitoring
For the tech industry, source code is the crown jewel, and its accidental or malicious leakage can be catastrophic.
VCS Integration: Deploy solutions that deeply integrate with your Version Control Systems (Git, GitHub, GitLab, Bitbucket) and internal code repositories.
Credential/Secret Detection: These tools scan commits and push requests for hardcoded credentials, API keys, private keys, and other sensitive information that could be accidentally committed and exposed.
IP Leakage Prevention: They monitor for unauthorized pushes to public repositories, large-scale cloning or downloading of proprietary code, and suspicious activity within the development pipeline, acting as a crucial line of defense against intellectual property theft.
5. Dark Web & Open-Source Intelligence (OSINT) Monitoring
Sometimes, the first sign of a leak appears outside your perimeter.
Proactive Reconnaissance: Subscribe to specialized dark web monitoring services that scan illicit marketplaces, forums, paste sites (like Pastebin), and private channels for mentions of your company, leaked credentials (emails, passwords), customer data samples, or even fragments of proprietary code.
Public Repository Scans: Regularly scan public code repositories (like public GitHub, GitLab) for inadvertently exposed internal code or configuration files.
Early Warning System: These services provide crucial early warnings, allowing you to invalidate compromised credentials, assess the scope of a leak, and respond before widespread damage occurs.
6. API Security Monitoring
Modern tech stacks are heavily reliant on APIs. A compromised API can be a wide-open door for data exfiltration.
API Traffic Baselines: Establish baselines for normal API call volumes, types, and user access patterns.
Anomaly Detection: Monitor for unusual API call spikes, unauthorized access attempts (e.g., using stolen API keys), attempts to bypass authentication/authorization, or large data extractions via API calls that deviate from normal usage.
Automated Response: Integrate API security solutions with your WAFs and SIEMs to automatically block malicious API requests or revoke compromised keys.
Beyond Detection: The Response Imperative
Detecting a leak is only half the battle. A well-rehearsed incident response plan is critical. This includes clear steps for containment, investigation, eradication, recovery, and communication. Regular tabletop exercises and simulations are vital to ensure your team can act swiftly and decisively when a leak is detected.
In 2025, data leaks are an existential threat to the tech industry. By adopting a multi-faceted, AI-driven detection strategy, deeply integrated across your infrastructure and focused on both human and technical anomalies, you can significantly enhance your ability to spot and stop leaks before they spiral into full-blown crises, safeguarding your innovation and maintaining customer trust.
0 notes
Text
CybersecurityNews: CyberEYE RAT Disables Windows Defender Using PowerShell and Registry Manipulations
0 notes
Text
China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malware
http://i.securitythinkingcap.com/TL32q2
0 notes
Text
Amazon Route 53 Resolver DNS Firewall prevents DNS threats

Amazon Route 53 DNS Firewall Advanced
Amazon Route 53 Resolver DNS Firewall protects against advanced DNS assaults.
Millions of applications simply connect users to their regular digital services using DNS queries. These queries connect with the internet's address book by transforming domain names like amazon.com into IP addresses computers need to route traffic. Amazon VPC DNS presents unique security risks and opportunities. DNS resolution can be used to manage network traffic before it starts. Second, the Amazon Route 53 Resolver, which runs separately from your internet gateway, routes DNS queries in your VPC to bypass other network security protections.
Start with standard domain lists to permit or prevent DNS resolution of specific domains, Amazon Route 53 Resolver DNS Firewall secures DNS traffic to handle this issue. AWS Managed Domain Lists automatically ban hazardous sites detected by Amazon Threat Intelligence and its trusted security partners. This method is successful against known dangers, but savvy thieves are increasingly using non-blocklist tactics.
Instead of static lists, Amazon Route 53 Resolver DNS Firewall Advanced provides intelligent protection. These advanced programs monitor DNS queries for suspicious tendencies like a security researcher. Even when the service finds unidentifiable domains, query duration, entropy, and frequency can indicate malicious activity. DNS tunnelling and domain generation algorithms (DGAs), which bad actors use to build covert communication channels or link malware to their command centres, are detected and stopped by this method.
Knowing DGA and DNS tunnelling risks
As mentioned, the Route 53 Resolver provides a service-managed internet access path separate from your VPC internet gateway. While DNS tunnelling allows DNS resolution, it can also be used to exploit its architecture. Let's explore these methods' operation and challenges.
DNS tunnelling utilises the DNS system's essential functionality by asking domain name questions and getting answers from the authoritative nameserver. Tunnelling encrypts DNS requests and answers instead of resolving domain names. A tunnelling exploit can use secretdata123.attacker.com, which contains encoded data, instead of just asking for example.com's IP address? Thus, DNS can be used for two-way command and control. DNS tunnelling must be identified and disabled to avoid data exfiltration and C2 connections.
DNS security is threatened by DGAs. Instead of utilising a set, predictable domain name that can be quickly halted, DGAs use mathematical techniques to produce many alternative domain names for C2 traffic. For instance, a DGA may generate mn9qrs.com tomorrow and xkt7py.com today. Effective blocklists are difficult to maintain since domains seem random and change constantly. DGA-generated domains are too rapid for typical threat intelligence feeds that find and block problematic sites.
DNS Firewall Advanced works how?
Route 53 Resolver DNS Firewall Advanced analyses domain names using several parameters to identify trustworthy and suspicious domains. Legitimate domain names, for instance, include real words and patterns to make them easier to remember and enter. However, DGA and tunnelling domains often feature weird patterns or random character sequences.
Route 53 Fix DNS Firewall Advanced analyses domain usage trends to provide insight. It learns what authentic domain names look like by monitoring the most resolved domains on the internet and AWS domain resolution trends. Using real-world training data helps establish domain name attributes. DNS Firewall Advanced analyses these patterns to DNS tunnelling and domain creation methods to identify suspicious behaviour.
Domain names are checked in several ways by the service:
Domain name structure and division
Use of letter and number patterns
How much the domain resembles natural language
Common words, not random characters
By analysing queries in real time and processing them in milliseconds, the service provides strong security without slowing your apps.
Route 53 Resolver DNS Firewall Advanced's configurable protection levels let you choose how aggressively to discover and address suspicious domains using confidence thresholds:
High confidence: Focussing on the biggest threats decreases false positives. It works well in production environments when blocking legitimate traffic is inconvenient.
Medium confidence: Protects most settings well.
Low confidence: The maximum detection level but may need adjustment to prevent false positives. High-security settings or preliminary traffic pattern monitoring benefit from this setup.
Mix these confidence levels with block or alert actions to create a security approach that meets your needs.
Observability
Route 53 Resolver query logging lets you see DNS requests from resources linked to your VPCs for security and compliance. Query logging can record the domain name, record type, response code, and originating VPC and instance for every DNS request. With the Route 53 Resolver DNS Firewall, query logging lets you monitor blocked queries and alter security rules to match your DNS traffic patterns.
Security Hub connection
Security Hub gives you an overview of your AWS security against industry standards and best practices. Security Hub collects security data from AWS accounts, services, and supported third-party products to identify the biggest security threats. These warnings will appear without further settings because it enables discoveries from both the Amazon: Route 53 Resolver DNS Firewall – AWS List and Advanced list. You only need to enable Amazon: Route 53 Resolver DNS Firewall – Custom List findings when using custom domain lists in rule groups.
In conclusion
Amazon Route 53 Resolver DNS Firewall Advanced protects businesses from complicated DNS-based attacks. The Route 53 Resolver bypasses security groups, NACLs, and the AWS Network Firewall while processing DNS queries, leaving many installations insecure. DNS tunnelling and DGA-based vulnerabilities exploit this blind spot, while Route 53 Resolver DNS Firewall Advanced employs anomaly detection and real-time pattern analysis to fight against them.
The AWS console was used to build up the service using the CloudFormation template and proposed rules that balance high-confidence threats and warnings. You saw how Security Hub integration centralises security findings and how query recording provides DNS traffic information. These features can protect your infrastructure from complicated DNS-based threats that standard domain blocklists cannot identify, improving cloud security and operational efficiency.
#AmazonRoute53ResolverDNSFirewall#AmazonRoute53Resolver#DNSFirewall#Route53Resolver#domaingenerationalgorithms#DNStunnelling#technology#technews#technologynews#news#govindhtech
0 notes
Text
Fast Flux Debrief

SIGNALFOG ENTRY: FAST FLUX AND THE NATIONAL SECURITY WIREWALK
What is Fast Flux?
Fast Flux is not a tool. It is a tactic—a slippery eel of cyber maneuvering used to shield malicious networks from takedown. At its core, Fast Flux is a technique for hiding phishing and malware delivery sites behind constantly changing IP addresses. Think of it as DNS shell game played at machine speed.
There are two main types:
Single-Flux – Frequently changes the IP addresses associated with a single domain name. A domain might resolve to five different IPs in under an hour. Those IPs are often bots in a compromised network.
Double-Flux – Mutates not only the IPs but also the name servers associated with the domain, creating a recursive maze of obfuscation. This is where things get nasty—each step reconfigures the puzzle.
Behind this flux cloud often sits a botnet, frequently leveraging criminal marketplaces or nation-state infrastructure, using the technique to hide:
Phishing sites
C2 (command and control) servers
Malware droppers
Credential harvesters
Why the NSA Considers It a National Security Threat
Fast Flux undermines attribution. In cyberwarfare, attribution is the new battleground. If you can’t pin an attack to an actor or infrastructure, you can’t deter, retaliate, or even understand intent. That makes Fast Flux a fog-of-war amplifier—a denial-of-attribution machine used not just by cybercriminals but by nation-state advanced persistent threats (APTs).
This tactic has been used to:
Distribute ransomware to critical infrastructure (e.g., Colonial Pipeline incident had partial DNS obfuscation elements)
Support long-term espionage operations (APT29 and others)
Exfiltrate sensitive data from government and defense contractors
It’s not just technical noise—it's sovereignty erosion via DNS.
Current Countermeasures
The countermeasures form a fragile ecosystem, not a silver bullet.
1. DNS Monitoring and Sinkholing
Agencies like US-CERT and NSA operate sinkholes—servers that simulate malicious domains to draw in Fast Flux queries and analyze them.
Security vendors offer passive DNS monitoring to correlate domain activity, TTLs (time-to-live), and ASNs (Autonomous System Numbers) that suggest flux behavior.
2. AI-Powered Anomaly Detection
Models trained on DNS query patterns identify abnormally high TTL churn, geographical dispersion of IPs, and unusually frequent domain-to-IP flips.
Emerging tools like PassiveTotal or Farsight DNSDB are leveraged to track malicious flux patterns.
3. Threat Intelligence Feeds
Enrichment of security tools with real-time feeds (e.g., from Mandiant, Recorded Future) to identify Fast Flux domains and block them at the firewall or endpoint level.
4. Domain Takedown Coordination
Multinational coordination with registrars and ISPs to revoke domains or neutralize the infrastructure (example: Operation Ghost Click, which dismantled DNSChanger infrastructure).
5. Advanced DNSSEC and DoH Filtering
DNS Security Extensions (DNSSEC) can help verify legitimacy, though flux domains often bypass this.
DNS over HTTPS (DoH) presents a double-edged sword: it can encrypt good and bad traffic alike. Thus, filtering on endpoints and proxies becomes essential.
6. Network-Level Behavioral Firewalls
Zero Trust Network Access (ZTNA) models segment networks to reduce botnet beaconing.
Behavioral IDS/IPS like Suricata detect lateral movement even if DNS resolution appears clean.
But Here's the Rub:
Fast Flux is not a flaw—it’s a clever exploitation of how the internet was designed to work: decentralized, resilient, fault-tolerant. The same qualities that make global communication work in disaster zones are co-opted to hide the hands of digital saboteurs. The NSA’s concern isn’t just technical—it’s existential. Because in the cyber-domain, whoever owns attribution owns the narrative.
“In war, truth is the first casualty; in cyberwar, it’s attribution.” — Anonymous NSA SIGINT Analyst, 2014 (declassified quote, attribution unknown...ironically)
0 notes
Text

20 Emerging Cybersecurity Trends to Watch Out in 2025
Businesses of all sizes, corporate entities, organizations, and even governments have embraced computerized systems to streamline daily operations. Consequently, ensuring cybersecurity has emerged as a paramount objective to protect data from many online threats and unauthorized intrusions. As technology evolves, so do cybersecurity trends, with data breaches, ransomware attacks, and hacks becoming increasingly commonplace. Elevate your expertise by enrolling in security courses led by industry experts, which will empower you with the knowledge and skills needed for comprehensive data protection.
The landscape of digital threats has undergone a profound transformation over the past few decades, driven by technological advancements and the digital interconnectedness of our world. As our society increasingly relies on digital technology for communication, commerce, and critical infrastructure, the threat landscape has evolved in complexity and sophistication. This detailed exploration will delve into the various facets of the evolving digital threat landscape, examining its key characteristics, emerging trends, and challenges to individuals, organizations, and governments.
One of the most notable trends in the digital threat landscape is the increasing sophistication of cyberattacks. Attackers constantly develop new techniques and strategies to breach security systems, steal sensitive data, or disrupt critical services. Various factors have driven this evolution, including the availability of powerful hacking tools, the proliferation of cybercrime forums, and the rise of nation-state-sponsored hacking groups.
Digital threats now encompass many attack vectors, including malware, ransomware, and DDoS attacks. These attack vectors have become more versatile, with attackers combining multiple methods to achieve their goals. For example, a ransomware attack may begin with a phishing email and escalate to the deployment of malware that encrypts data.
#sciencefather#PetroleumGeologist, #Oceanographer, #Hydrographer, #SoilScientist, #EnvironmentalConsultant, #ConservationScientist,#VeterinaryScienceAward, #BiomedicalScienceAward, #GeneticsAward, #NeuroscienceAward, #PharmacologyAward, #ChemistryAward, #PhysicsAward, #GeologyAward, #AstronomyAward, #OceanographyAward
International Young Scientist Awards
Website link: youngscientistawards.com
NominationLink:https://lnkd.in/eBZm-dJV
Contact Us: [email protected]
___________________________________
Social Media:
Twitter : https://lnkd.in/eBYdsWMn
Linkedin- : https://lnkd.in/ez_rQ-C2...
Pinterest : https://lnkd.in/eeW4ZBbH...
Blog : https://youngscientistaward.blogspot....
Tumblr : https://lnkd.in/eKb7dXrM
0 notes